Next up on hackers’ IoT target list: Gas stations

CANCÚN, Mexico—You can add gas stations to the growing list of real-world hacking targets. Two security researchers in Israel have new evidence that gas station systems, from cash registers to fuel pumps, are connected to the Internet and exposed to malicious hackers.
The researchers who discovered the vulnerability, Ido Naor, a senior security researcher at Kaspersky Lab, and Amihai Neiderman, an independent researcher formerly at Azimuth Security, found gas stations connected to the Internet through Shodan, a public search engine of the Internet of Things.
Thanks to hard-coded default usernames and passwords, they say, they were able to change the price of gas charged at a gas station in Israel that cooperated with the researchers. Naor says once they had hacked into the gas station’s online management system, they could have manipulated or even shut down the station’s underground fuel tanks or pumps, stolen gas, hacked security cameras, or skimmed payments from the on-site convenience store or at the pump.
READ MORE ON THE INTERNET OF THINGS
For decade-old flaws in voting machines, no quick fix
Critical systems at heart of WannaCry’s impact
Time for a Department of the Internet of Things?
The long reach of Mirai, the Internet of Things botnet
Hackers call for federal funding, regulation of software security
Shut the front door: The state of the ‘smart’ lock
5 questions to ask before buying an IOT device
Living on the edge of heartbreak: Researcher hacks her own pacemaker
They had “full access” to the system, Naor told The Parallax at the annual Kaspersky Security Analyst Summit (co-sponsored by Avast Software, which sponsors this site) here last Friday, where they presented research that was first published in Motherboard at the end of January. “We joked we could make it explode, but we don’t know for sure.”
The specific system that they found the vulnerabilities in, SiteOmat management software, is made by Israel-based Orpak Systems, which, according to its site, supplies monitoring and management equipment to more than 35,000 gas stations globally, including those associated with Shell, BP, Indian Oil, and the New Hampshire Department of Transportation. Neither Naor nor Orpak, whose competitors include Wayne Fueling Systems and Fairbanks Environmental, would specify which stations were affected.
The software is designed to allow station owners to manage one station, or a network of them. If even one station in a network is improperly protected, then a hacker could get access to any of them, Naor says. Most SiteOmat system connections are properly protected, he says. But “more than 1,000” gas stations running it are vulnerable, 29 percent of which are in India and 27 percent in the United States.
Naor complained that when he and Neiderman contacted Orpak Systems and its parent company, Gilbarco Veeder-Root, last September about their findings, neither company cooperated. After they shared their research, Naor says, the companies “ghosted” on them, refusing to respond to further attempts at communication, including emails, phone calls, and messages sent via mobile-messaging app WhatsApp.
Orpak denied “elements” of the Kaspersky report in an emailed statement to The Parallax, saying parts of the report are “inaccurate” and “not relevant” because many of the affected stations are private, used to serve corporate-vehicle fleets, and not accessible to consumers. (All stations that use Orpak software in the United States, it said, serve only corporate fleets.) However, a gas station serving a private vehicle fleet can still be susceptible to fraud and hacking, as corporate-fleet owners and gas stations still have to pay for fuel.
Orpak has “implemented” security patches and software upgrades, wrote Aviv Tal, vice president of strategy and marketing for Orpak. “Sites where there may be vulnerabilities have been notified to implement additional IT security measures to reduce or eliminate risks.” In a follow-up email, Tal declined to specify what had been patched, or what parts of the report were incorrect.
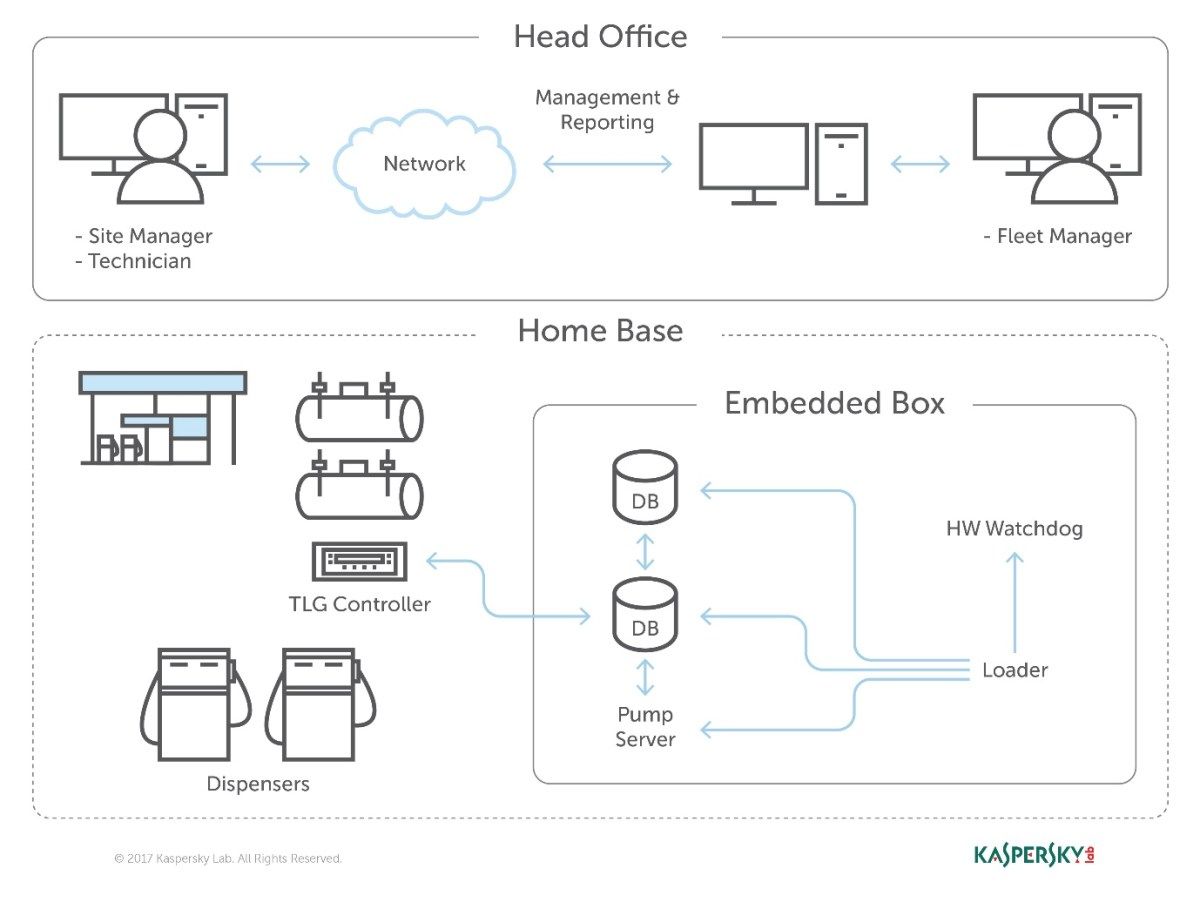
How a network running Orpak software accesses and manages the controller unit and access privileges. Illustration courtesy Kaspersky Labs.
The revelation that gas stations running Internet-connected software are potentially exposed to hackers echoes those of numerous other industries. The Internet of Things, the multitude of hardware devices connected to the Internet, from baby monitors to door locks to security cameras to cattle trackers, extends to businesses, and can expose both consumers and business owners to fraud. Call it an Industrial Internet of Things.
General Electric, which has invested heavily in the Industrial Internet of Things, including gas stations, health care, transportation, and control systems for critical infrastructure such as water and power, predicts that IIoT will be a $225 billion market by 2020.
The problem is that not enough of those hundreds of billions of dollars will be spent on securing the devices, says Bryson Bort, a leading researcher and founder at the intersection of the Internet of Things and industrial control systems.
“This is about more than connecting to the Internet. This is about connecting to the Internet without thinking about it,” says Bort, founder of the cybersecurity consultancies Grimm and Scythe. “Orpak didn’t demonstrate basic best practices.”
Among the mistakes Oprak made, Bort argues, is that it hard-coded system log-in credentials. Anyone with access to the system could change gas prices without additional log-in credentials. Another problem is that Orpak’s hardware isn’t easy to update, or even replace, he says.
“These things were designed to be put in place and forgotten about until they broke,” Bort says, adding that the company’s lack of security hygiene and foresight, combined with its lackluster response, put its customers at risk. “The thing that’s missing is accountability.”
